
As we know SQL (Structured Query Language), is used to retrieve and manipulate data in relational databases. And the database can be hacked with this SQL too. They call it as “SQL Injection”. Let us understand how this SQL injection technique is used to hack the websites.
Wait ! This does not mean , I’m going to write about how to hack any website with SQL injection and you would try it on Facebook or Instagram. Nothing like this is going to happen. This article will be helpful to make your web application project invulnerable against SQL Injection hacking .
Let us take one example of website login page to feel this concept. Generally there are 2 fields viz., User name and Password. We already know that, we use GET and POST methods (from PHP ) to insert the data from Login page into our Database table.
1. GET method:
When GET is implemented, we pass the actual values of ID and password from URL field. In simple words ,we can see ID and password in the link itself. And this is the hack. We will be logged in by editing this field as, username=”OR 1=1 —
- ‘1’ = ‘1’ is a condition that will always be true, thereby it is accepted as a valid input by the application
- –(double hyphen) instructs the SQL parser that the rest of the line is a comment and should not be executed
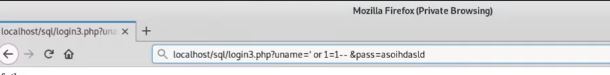
Any random password can work here. Try this for your site on local host for better understanding.
Hence we can conclude, first way to make the system invulnerable is to avoid GET method for inserting data in database.
2. POST method :
Like GET, in this method username and password are not visible in URL field. So there is no way to insert SQL in URL. Hackers use above same trick of malicious string but in Username field. At Username field, write as ”OR 1=1 — and type any random password. You will be logged in.

Any random password can also work here. If not, they use same malicious string in password field too. At back end, SQL Query is run as shown below:

You might have thinking SQL injection is this much easy. Yes, it is easy but every drug has its antidote too. There are many ways to prevent such hacking .
One of it is to use bind parameter in Database connectivity code as below:

Bind parameter binds whole input together and considers it as one string. In simple words, malicious string ”OR 1=1 — works as input and any operation is not performed.
Other than this, there are many ways to prevent SQL Injection like Input Validation using Regular Expressions and Restricting number of characters in password field.
Do implement above methods in your code while developing web applications and share with your friends.


Leave a comment