In the earlier part of log4j, we saw what log4j is and how is it affecting the enterprises. In this blog, we will see, how can we exploit Log4j vulnerability. But before going ahead, let us understand below two terms:
- LDAP- (Lightweight Directory Access Protocol) :
It is open source standard application protocol for accessing and maintaining distributed directory information.
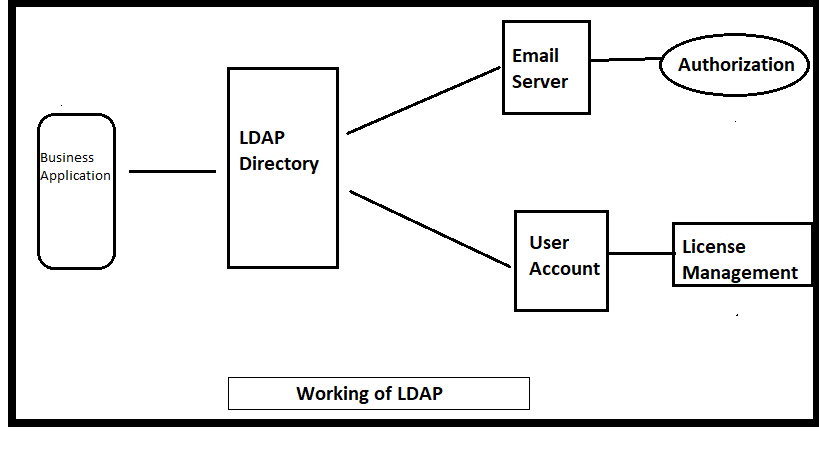
For example: Suppose you register in an business application using your username and password. Now LDAP comes here to store your information in user accounts and whenever you login in application then it sends request to LDAP. LDAP verifies your identity and throws Authorization server. If credentials are correct then it allows to log in.
2. JNDI – (Java Naming & Directory Interface) :
JNDI provides an API for application to interact with LDAP. In simple words, Java application cannot directly request LDAP because of this, we need JNDI which gives a way to interact with LDAP.

Now let’s see, how can we exploit Log4j vulnerability:
Log4j allows logged messages to contain format strings that reference external information through JNDI. This allows information to be remotely retrieved across variety of protocols including LDAP.
The contents of the message often contain user-controlled data. Attackers can insert JNDI reference pointing to LDAP servers they control, ready to serve malicious java classes that perform any action they choose.
Mitigation:
1. Vendor has released a fix and customers are advised to update Log4j to version 2.17.0, if updating version is possible.
2. Using ongoing firewall rules on servers is a good mitigation technique to prevent attackers.


Leave a comment